Security Issue Fix Release: 0.99.6 and 0.0.8
This release fixes security issue existing in CppCMS 1.x.x version <= 0.99.5 and CppCMS 0.0.x <= 0.0.7.
The Issue
Who is affected?
Users who use AES encrypted cookies for session data storage
What is the risk
Attackers may create a session data that wasn't generated by the CppCMS application - so basically attacker may change the content of the session to something else. And potentially, for example, gain some rights that he does not have.
What is not exposed
The privacy of the data stored in the session is not affected.
Recommendations
It is recommended to upgrade to latest CppCMS version.
Workaround
If it is not possible and you are using AES encrypted cookies as sessions storage, do one of the following:
- Switch to "hmac" signed cookies if the data that is stored in cookies is not confidential.
- Switch to server side session storage.
Detailed Description
The Problem Description
The redundancy check of AES encrypted session cookies was too weak, allowing attacker to create cookies that would look like valid cookies generated by CppCMS but they would contain an invalid content.
More detailed, the cookies where created as following:
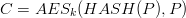
Where k is secret key, P is the encoded data and C the cookies stored at client side.
However this scheme is weak and does not really protect against creation of invalid content. There are known attacks against 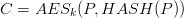 , I assume attacks against the scheme above can be created as well.
, I assume attacks against the scheme above can be created as well.
The Fix Provided
The cookies data is now encrypted and signed as:
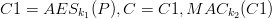
Where MAC is HMAC-SHA1 k1, k2 are keys that are either provided or generated from the source key k as 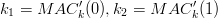
Additional Configuration Options (CppCMS 1.x.x)
Added a way to provide explicit MAC and encryption algorithm:
- session.client.hmac - the HMAC algorithm: md5, sha1, sha192, sha256, sha384 and sha512
- session.client.hmac_key - the key for MAC
- session.client.cbc - the encryption algorithm aes, aes128, aes192, aes256
- session.client.cbc_key - the key for encryption algorithm
You may specify only hmac and hmac_key and then the cookies would be only "signed", of you specify cbc and cbc_key they would be also encrypted.
When you use the current method specifying session.client.encryptor with "aes" then HMAC-SHA1 would be used ensure authentication and the MAC and encryption keys would be generated from the provided session.client.key.
You may also store the key in file and use:
session.client.hmac_key_filesession.client.cbc_key_filesession.client.key_file
Instead of
session.client.hmac_keysession.client.cbc_keysession.client.key
The file pointed by this value is a text file that holds hexadecimal representation of the key you need to use.
These keys are read before switching the user and forking allowing to make these keys files to be non-readable in the normal run-time.
CppCMS 0.0.8 AES Encryption
It uses AES128 for secrecy and HMAC-SHA1 for authentication, the keys for each one of them are generated from the single key provided in the configuration file.
Additional Bug Fixes:
- Fixed incorrect url-encoding that also included buffer overflow in CppCMS 1.x.x
- Fixed bas64_urlencode filter.


Comments
Thanks for update!
Add Comment:
You must enable JavaScript in order to post comments.